In the last few weeks, Bitcoin Silent Payments, or BIP-352, have started being deployed in various wallets. In this article, we will explain what Bitcoin Silent Payments are and how to detect their usage.
Stealth Addresses
Bitcoin addresses are always transparent. For every Bitcoin transaction, anyone can see the sending and receiving addresses for each enote (UTXO), which means they can see the entire transaction history and BTC balance for each address. This has undesirable privacy characteristics compared with cash and bank transfers, where these transfers and balances are not known in a public database.
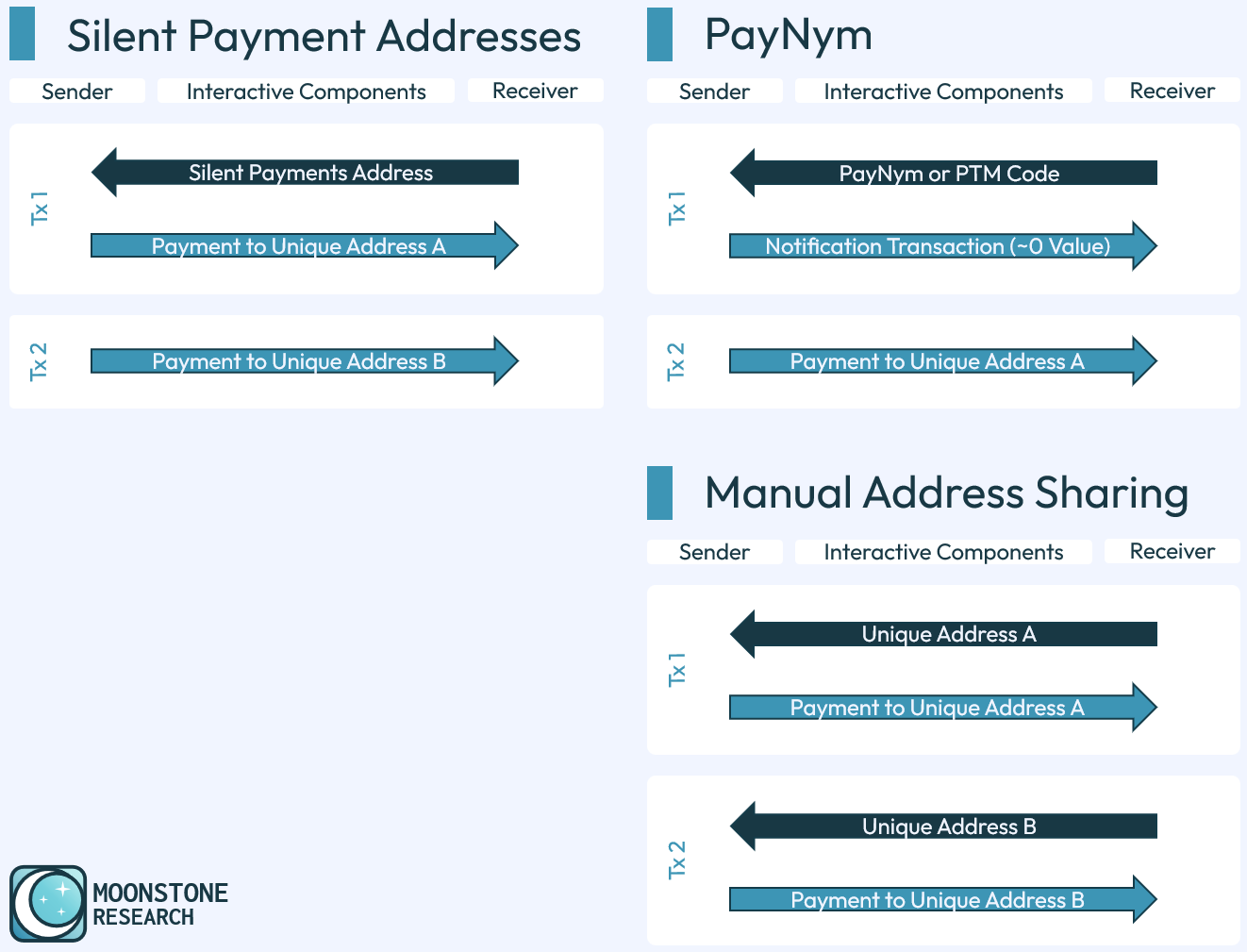
To address these challenges, Bitcoin users have the option to generate and provide a new address for each transaction. Using new addresses isn't enough on its own to provide the same degree of privacy as cash transactions, but it makes it more difficult for outside observers to track the use of their funds.
A major downside of manually generating and providing a new address is that it is an interactive process. A recipient must manually provide the sender with a new address every time they wish to receive a payment.
Silent Payments address this problem. Silent Payments allow recipients to provide a special Silent Payments address to a sender, and this sender can automatically generate unique receiving addresses without any further communication with the receiver.
Silent Payments have the potential to increase privacy wherever addresses are currently reused.
If you wish to learn more about the cryptography that allows Silent Payments to work, we recommend that you read BIP-352.
Institutional Applicability
Privacy isn't only for criminals. Financial institutions may prefer to use Silent Payments for greater privacy than reusing addresses.
Many exchanges and custodians require additional security checks to add and remove withdrawal addresses. These security checks make it more difficult for an employee to incorrectly provide a wrong address, or for a hacker to replace a legitimate address with an illicit address.
An unfortunate consequence of these security measures is that this effectively forces address reuse between institutions.
With Silent Payments, exchanges and custodians can securely "lock in" a single Silent Payments address for a counterparty, and they can enjoy the privacy benefits of unique addresses for each transaction without the security risk of switching addresses. Exchanges can create multiple Silent Payments addresses within the same wallet seed, which allows them to easily determine which customer to credit for a given deposit.
Scanning Downside
Silent Payments have a major downside that will negatively impact their adoption: scan time. Silent Payments recipients must actively scan the Bitcoin blockchain for new incoming transactions that are sent to their Silent Payments addresses. This is similar to Monero wallet scanning. If a user needs to scan several weeks of months of Bitcoin history, then this wallet scanning could take several minutes or even hours.
Scanning can be optimized with the help of a trusted Bitcoin node. The scanning process can be delegated to the node instead of performed by the wallet. Although this will leak significant payment information to the node, some advanced users may run their own nodes with a scanning function and connect to their own nodes.
Detecting Bitcoin Silent Payments
One major privacy advantage of Bitcoin Silent Payments transactions is that they appear like normal Taproot transactions.
Here is an example Silent Payments address:
sp1qqfk0ag4gmq87agdy8lawrlt2mf3p8myhkuxgp5s7kdck4ywwg7mjjqc2wmmtfddvevmjnlv4klmgsx4g79rr998d20r5vmxera5f2a54nu5h496v
According to the BIP-351 specification, Bitcoin Silent Payments (specifically v0) can be detected through the following:
- Silent Payments addresses (NOT the addresses that appear on-chain in transactions) always start with "sp1q" and are 116 characters long.
- Silent Payments receiver outputs are always BIP341 Taproot outputs (the address should start with "bc1p").
Impact on Investigations
Investigators regularly search for high-risk Bitcoin addresses, since they have been used for terrorist fundraising efforts and other illicit efforts.
Historically, exchanges and investigators have searched for all transactions that interact with these high-risk and illicit addresses. The static donation addresses and all associated transactions could be attributed and screened for as a part of an exchange compliance program.
Some threat actors used more sophisticated methods such as running their own self-hosted payment processor to avoid address reuse. However, even unsophisticated actors can now provide a static Bitcoin Silent Payments address on their website. With a Bitcoin Silent Payments address, it is not possible to search for all transactions that relate to that address.
If adopted by terrorists and other illicit actors, Bitcoin Silent Payments will make the passive surveillance of their activities more difficult. Investigators will need to rely on more active measures and advanced blockchain analysis techniques to learn about these activities.
Exchanges can still use screening tools to check for any requested withdrawals to a suspicious Silent Payments address, since exchanges will learn what Silent Payments address a customer is withdrawing to (even though that information is hidden from the public). Thus, information-sharing between exchanges and law enforcement will be more important than ever. Exchanges should update their own address screening tools or work with their address screening vendors to support suspicious Silent Payment addresses, even if exchanges do not support withdrawals to Silent Payment addresses.
Adoption Challenges
Ultimately, illicit actors will only use Silent Payments if they are adopted in common wallet software. For illicit actors to raise donations through a Silent Payments address, donors' wallet software needs to support sending to a Silent Payments address.
Illicit actors may find some success in encouraging potential donors to use special, niche wallet software, but there have been very few successful efforts like this so far. Illicit actors' willingness to accept Bitcoin and Ethereum donations shows that the top priority is accepting money that their donors can easily acquire and use, not pushing people to use more-private payment methods such as Monero.
Alternative Approaches
Bitcoin Silent Payments are similar to other approaches to stealth address techniques on Bitcoin.
BIP-47 PayNyms
BIP-47, best popularized through PayNyms used in Samourai Wallet, allow for a sender to automatically generate a new receiver address.
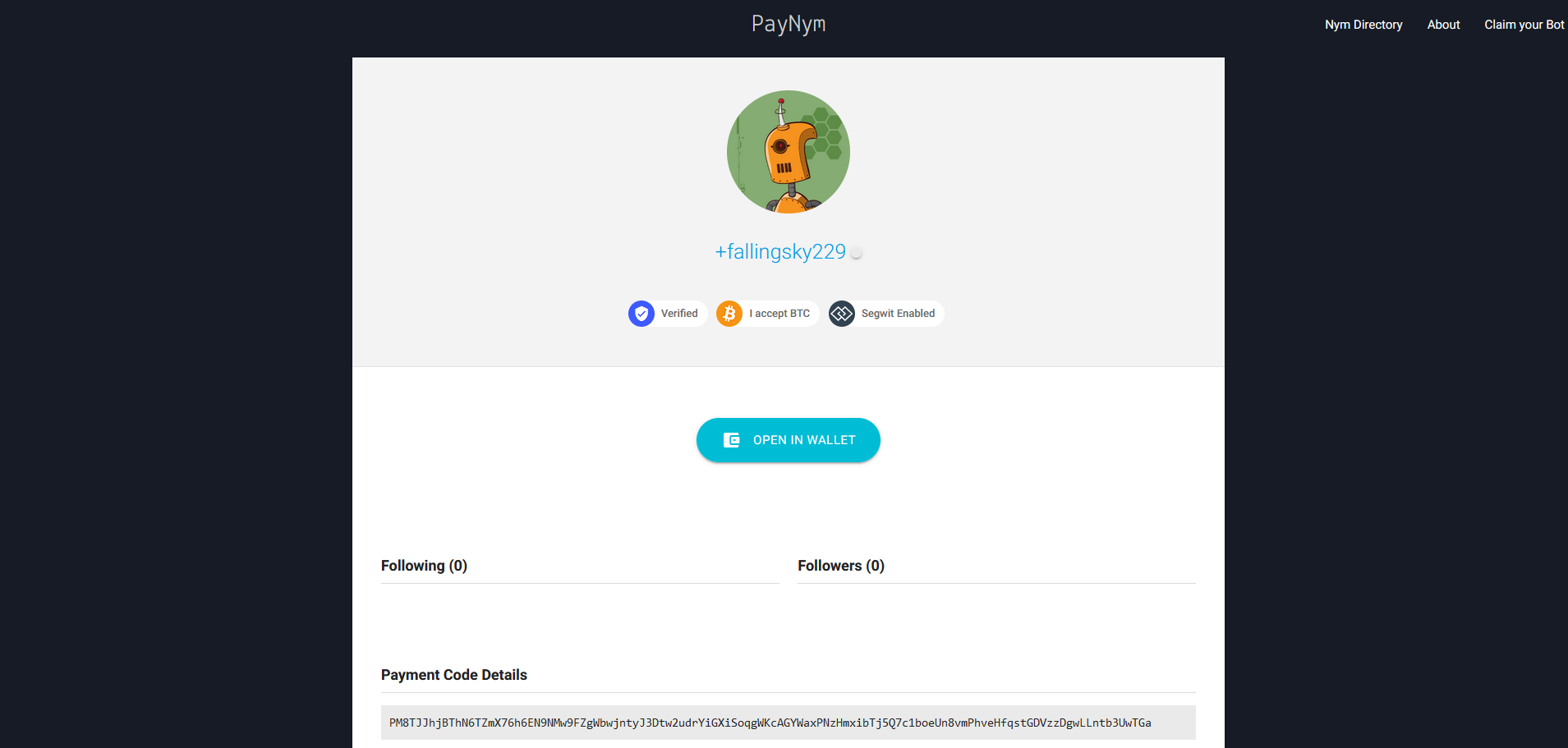
Here is an example BIP-47 payment code:
PM8TJJhjBThN6TZmX76h6EN9NMw9FZgWbwjntyJ3Dtw2udrYiGXiSoqgWKcAGYWaxPNzHmxibTj5Q7c1boeUn8vmPhveHfqstGDVzzDgwLLntb3UwTGa
PayNym.is served as a centralized database to connect human-readable names to these payment codes. For example, "+fallingsky229" is assigned to the PMT code above.
Although Samourai Wallet used a centralized database to simplify the sharing of these human-readable PMT codes, no centralized database is required. Users can share these PMT codes manually, or they could be shared through a more decentralized method such as domain DNS records.
BIP-47 has a significant privacy drawback. Before a sender can generate new addresses for the recipient, the sender must first make a "connection" or "notification" transaction to the a static recipient notification address. This leaves an on-chain, public signature that essentially says "this transaction was made by a sender who wishes to pay this specific BIP-47 user in the future."
For a specific PayNym, an outside observer can look up all transactions that have "connected" with it for future payments. There's no direct way to associate these future payments with the notification transaction, but advanced blockchain analysis techniques may still be able to link these actions together.
Different variants of BIP-47 exist that allow for the notification transaction to be sent in different ways, but the ultimate downside of the on-chain message is the same.
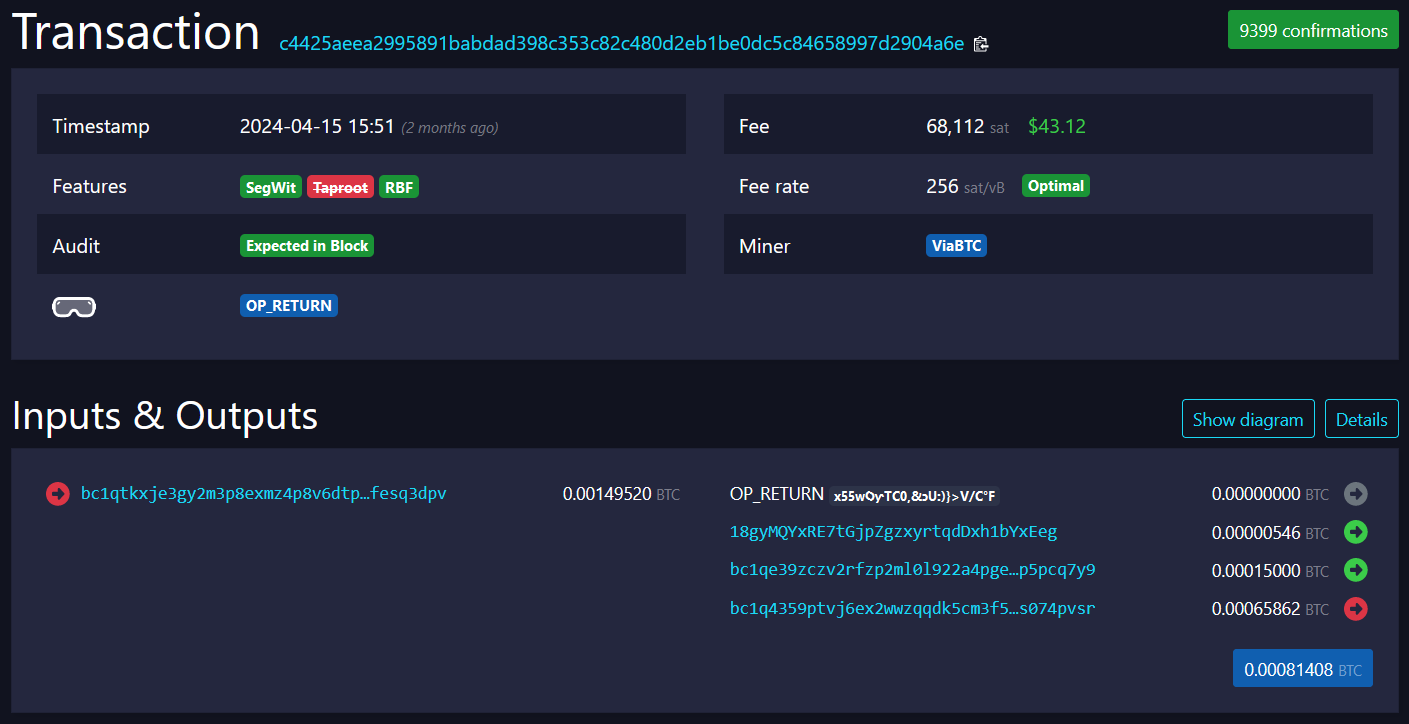
Looking at this PayNym notification address with over 2000 transactions, you can see that the vast majority contain four entries on the "output" side of the transaction. For this transaction, the output side contains:
- OP_RETURN
- 0.00000546 BTC to 18gyMQYxRE7tGjpZgzxyrtqdDxh1bYxEeg (notification address)
- 0.00015 BTC to bc1qe39zczv2rfzp2ml0l922a4pgetj63tp5pcq7y9 (fee paid to Samourai)
- 0.00065862 BTC to bc1q4359ptvj6ex2wwzqqdk5cm3f5xmqr7s074pvsr (change)
Notification transactions typically follow this format.
Payment Processor
Although not technically a stealth address approach, Bitcoin payment processors help recipients provide a unique address for each transaction. Payment processors can be run on relatively inexpensive hardware, including a Raspberry Pi.
Bitcoin payment processors can be run by a third party (such as BitPay), but privacy-conscious users will opt to run their own software that does not rely on a third party. We expect that darknet websites will use self-hosted payment processors and/or Bitcoin Silent Payments if they haven't already.
Summary
Bitcoin Silent Payments are here, and exchanges and investigators should prepare to encounter them in the wild. Silent Payments allow for senders to create multiple transactions to unique addresses without receiver interactivity. Though Silent Payments are not a comprehensive privacy solution on their own, they make it easier for individuals and institutions to use fresh addresses.
About Moonstone Research
Moonstone Research is a boutique blockchain analysis firm that investigates difficult-to-trace transactions. We specialize in tracing ransomware and other illicit payments. We also assist compliance professionals with supplementary investigations and reporting. Please email us if you would like to get in touch.